TIDUE59A May 2018 – September 2020
- Description
- Resources
- Features
- Applications
- 1System Description
-
2System Overview
- 2.1 Block Diagram
- 2.2 Design Considerations
- 2.3 Highlighted Products
- 2.4 System Design Theory
- 3Hardware, Software, Testing Requirements, and Test Results
- 4Design Files
- 5Software Files
- 6Related Documentation
- 7Terminology
- 8About the Author
- 9Revision History
2.4.7 Over-the-Air Updates
An OTA update refers to a software update that is wirelessly transferred and installed on a system. Wi-Fi-enabled systems can receive software updates directly from cloud servers, which makes it easier for vendors to distribute software updates to a large number of devices deployed across different regions and in various locations.
It is important for all products that connect to peers through the Internet to support software updates, because they are necessary to ensure that components of the software that enable security features stay up-to-date over the lifetime of a product. For example, the files needed to support TLS authentication and connect with a peer through the Internet may need to be updated over time. In addition to supporting the security life-cycle of a product, software updates also let developers enable new features for end customers after the product is sold.
The SimpleLink Wi-Fi SDK includes an OTA library that can be used to quickly implement OTA updates in an application. The library includes support for both Dropbox and GitHub APIs, but the libray can also be modified to support alternate content delivery networks (CDN). The TIDC-01005 demonstrates an OTA update solution for a Wi-Fi electronic smart lock using the OTA library with the Dropbox API.
The OTA process in the wifi_doorlock application is implemented in a software task that executes its own state machine. When the OTA task starts, it prevents the user from triggering an OTA update until the system has successfully connected to a local network and acquired an IP address. When connected, the task enters an idle state where it remains until an OTA update is triggered by the user. The user can trigger an OTA update by using MQTT to publish a message to the CC3220 device on the LockOTA topic. When started, the OTA task enters the OTA Run State, where the task downloads the components of the software update and writes the update to the file system until the update is complete. After all the components are downloaded and have been stored on the external serial flash, the OTA task sends a reset request to the control task, to trigger the system to reboot and run with the updated software.
Figure 2-10 shows a diagram of the state machine implemented by the OTA task.
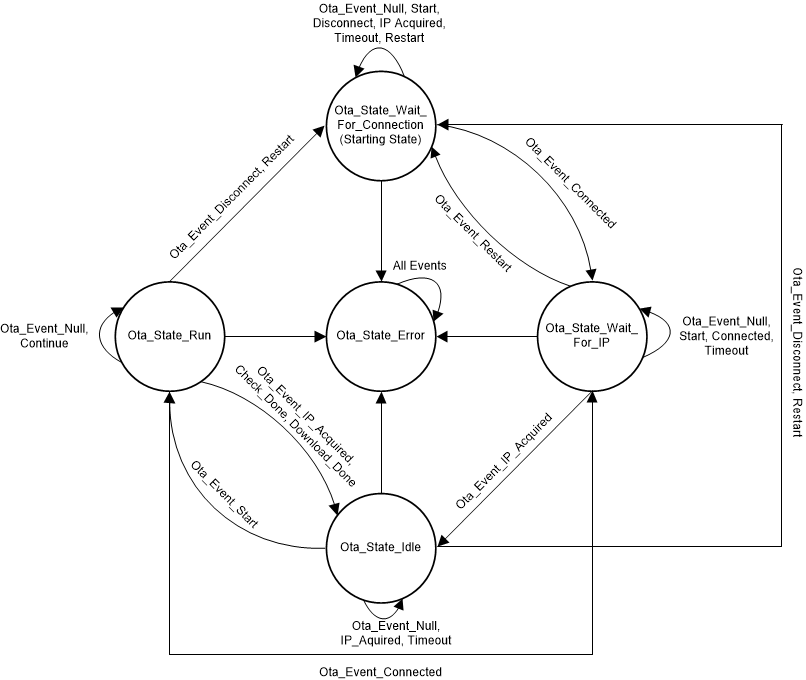 Figure 2-10 OTA Task State Machine
Figure 2-10 OTA Task State Machine