SLAA721E October 2016 – March 2020 MSP430FR5969 , MSP430FR5969-SP , MSP430FR5994 , MSP430FR6989
- Trademarks
- 1Introduction
- 2Implementation
- 3Customization of MSP430FRBoot
- 4Building MSPBoot
- 5Demo Using FRAM LaunchPad Development Kit as Host
- 6Porting the target side example projects to other MSP430FR devices
- 7References
- 8Revision History
2.2.1.2 Application Validation
The application validation mechanism allows the bootloader to validate the application before executing it. Three methods are implemented to allow for different levels of code footprint and security:
-
Single image mode (new application will download directly into the application area)
-
Two options can be used in this mode (Defined in TI_MSPBoot_Config.h):
-
Level_1: Checks if the reset vector is empty (0xFFFF)
-
Level_2: Does CRC in the application area and uses the CRC result to compare with the CRC signature that is located at the start of the application memory
-
-
-
Dual image mode (new application will download into a dedicated area and copy into the application area after the CRC check)
Figure 2-4 shows the implementation of the validation process in dual image mode.
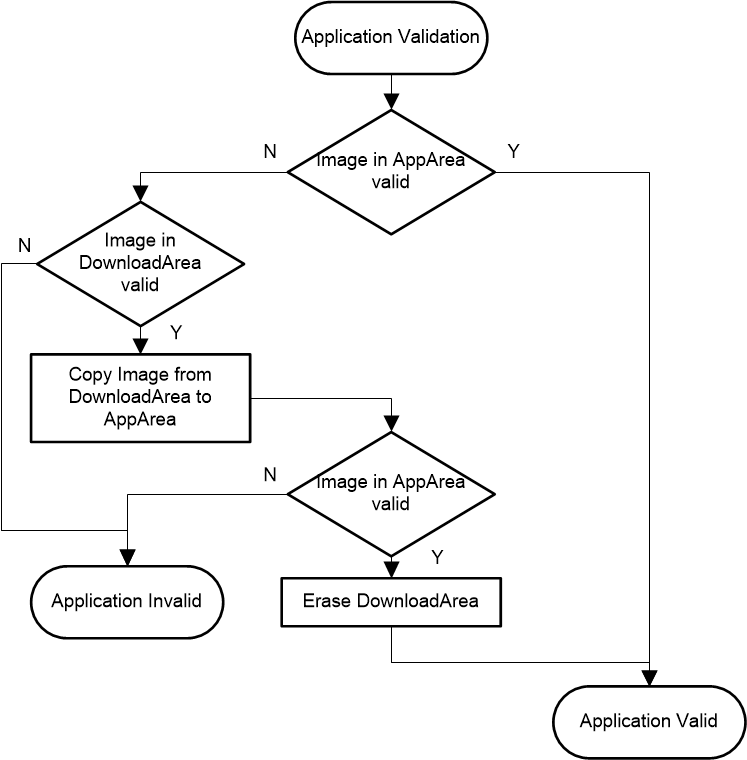 Figure 2-4 Dual Image Application
Validation
Figure 2-4 Dual Image Application
ValidationThe validation methods can prevent executing corrupted applications but they do not ensure the integrity and functionality of the application, which is the user’s responsibility. If the application does not have the intended functionality, the MSP430 can still be recovered using a hardware entry sequence.
When an application download process is completed, MSPBoot performs the following steps before jumping to the new application:
-
Validate the new image in the Download area.
-
If invalid, exit. A reset forces the bootloader again and executes the application only if the original image is valid.
-
Continue otherwise.
-
-
Replace Application area with Download area.
-
Validate image in Application area.
-
If valid, erase Download area. A reset will execute the application, because the image in the Application area is valid.
-
Exit otherwise. This is an unexpected state, but a reset will validate both images again.
-