SFFS022 December 2022 TMS320F28384D , TMS320F28384D-Q1 , TMS320F28384S , TMS320F28384S-Q1 , TMS320F28386D , TMS320F28386D-Q1 , TMS320F28386S , TMS320F28386S-Q1 , TMS320F28388D , TMS320F28388S
- Safety Manual for TMS320F2838xD and TMS320F2838xS
- Trademarks
- 1Introduction
- 2TMS320F2838x Product Safety Capability and Constraints
-
3TI Development Process for Management of Systematic Faults
- 3.1 TI New-Product Development Process
- 3.2 TI Functional Safety Development Process
- 3.3 C2000 Architecture and Product Overview
- 3.4
Functional Safety Concept
- 3.4.1 VDA E-GAS Monitoring Concept
- 3.4.2 TMS320F2838xD/S MCU Safety Philosophy
- 3.4.3 Fault Tolerant Time Interval (FTTI)
- 3.4.4 TMS320F2838x MCU Safe State
- 3.4.5 Assumed Safety Requirements
- 3.4.6 Operating States
- 3.4.7 Management of Faults
- 3.4.8 Suggestions for Improving Freedom From Interference
- 3.4.9 Suggestions for Addressing Common Cause Failures
- 4TMS320F2838x Diagnostics Libraries
-
5Brief Description of Safety Elements
- 5.1 C2000 MCU Infrastructure Components
- 5.2 Processing Elements
- 5.3 Memory (Flash, SRAM and ROM)
- 5.4 On-Chip Communication Including Bus-Arbitration
- 5.5
Digital I/O
- 5.5.1 General-Purpose Input/Output (GPIO) and Pin Muxing
- 5.5.2 Enhanced Pulse Width Modulators (ePWM)
- 5.5.3 High Resolution PWM (HRPWM)
- 5.5.4 Enhanced Capture (eCAP)
- 5.5.5 High Resolution Capture (HRCAP)
- 5.5.6 Enhanced Quadrature Encoder Pulse (eQEP)
- 5.5.7 Sigma Delta Filter Module (SDFM)
- 5.5.8 External Interrupt (XINT)
- 5.6 Analog I/O
- 5.7
Data Transmission
- 5.7.1 Controller Area Network (DCAN)
- 5.7.2 ECAT
- 5.7.3 Serial Peripheral Interface (SPI)
- 5.7.4 Serial Communication Interface (SCI)
- 5.7.5 Inter-Integrated Circuit (I2C)
- 5.7.6 Fast Serial Interface (FSI)
- 5.7.7 Power Management Bus Module (PMBus)
- 5.7.8 Multichannel Buffered Serial Port (McBSP)
- 5.7.9 External Memory Interface (EMIF)
- 5.8 Not Safety Related Elements
-
6Brief Description of Diagnostics
- 6.1
C2000 MCU Infrastructure Components
- 6.1.1 Clock Integrity Check Using CPU Timer
- 6.1.2 Clock Integrity Check Using HRPWM
- 6.1.3 EALLOW and MEALLOW Protection for Critical Registers
- 6.1.4 Efuse Autoload Self-Test
- 6.1.5 Efuse ECC
- 6.1.6 Efuse ECC Logic Self-Test
- 6.1.7 External Clock Monitoring via XCLKOUT
- 6.1.8 External Monitoring of Warm Reset (XRSn)
- 6.1.9 External Voltage Supervisor
- 6.1.10 External Watchdog
- 6.1.11 Glitch Filtering on Reset Pins
- 6.1.12 Hardware Disable of JTAG Port
- 6.1.13 Internal Watchdog (WD)
- 6.1.14 Lock Mechanism for Control Registers
- 6.1.15 Missing Clock Detect (MCD)
- 6.1.16 NMIWD Reset Functionality
- 6.1.17 NMIWD Shadow Registers
- 6.1.18 Multibit Enable Keys for Control Registers
- 6.1.19 Online Monitoring of Temperature
- 6.1.20 Periodic Software Read Back of Static Configuration Registers
- 6.1.21 Peripheral Clock Gating (PCLKCR)
- 6.1.22 Peripheral Soft Reset (SOFTPRES)
- 6.1.23 Software Test of Reset (Type 1)
- 6.1.24 PLL Lock Profiling Using On-Chip Timer
- 6.1.25 Reset Cause Information
- 6.1.26 Software Read Back of Written Configuration
- 6.1.27 Software Test of ERRORSTS Functionality
- 6.1.28 Software Test of Missing Clock Detect Functionality
- 6.1.29 Software Test of Reset
- 6.1.30 Software Test of Watchdog (WD) Operation
- 6.2
AUXPLL
- 6.2.1 Clock Integrity Check Using DCC
- 6.2.2 PLL Lock Indication
- 6.2.3 Internal Watchdog (WD)
- 6.2.4 Software Test of DCC Functionality Including Error Tests
- 6.2.5 External Clock Monitoring
- 6.2.6 Software Test of PLL Functionality Including Error Tests
- 6.2.7 Interleaving of FSM States
- 6.2.8 Dual Clock Comparator (DCC) – Type 1
- 6.2.9 Peripheral Access Protection - Type 0
- 6.3
Processing Elements
- 6.3.1 CLA Handling of Illegal Operation and Illegal Results
- 6.3.2 CLA Liveness Check Using CPU
- 6.3.3 CPU Hardware Built-In Self-Test (HWBIST)
- 6.3.4 CPU Hardware Built-In Self-Test (HWBIST) Auto-Coverage
- 6.3.5 CPU Hardware Built-In Self-Test (HWBIST) Fault Injection Capability
- 6.3.6 CPU Hardware Built-In Self-Test (HWBIST) Timeout Feature
- 6.3.7 CPU Handling of Illegal Operation, Illegal Results and Instruction Trapping
- 6.3.8 Reciprocal Comparison by Software
- 6.3.9 Software Test of CLA
- 6.3.10 Stack Overflow Detection
- 6.3.11 VCU CRC Check of Static Memory Contents
- 6.3.12 VCU CRC Auto Coverage
- 6.3.13 Embedded Real Time Analysis and Diagnostic (ERAD)
- 6.3.14 Inbuilt hardware redundancy in ERAD bus comparator module
- 6.3.15 Disabling of Unused CLA Task Trigger Sources
- 6.4
Memory (Flash, SRAM and ROM)
- 6.4.1 Bit Multiplexing in Flash Memory Array
- 6.4.2 Bit Multiplexing in SRAM Memory Array
- 6.4.3 Data Scrubbing to Detect/Correct Memory Errors
- 6.4.4 Flash ECC
- 6.4.5 Flash Program Verify and Erase Verify Check
- 6.4.6 Software Test of ECC Logic
- 6.4.7 Software Test of Flash Prefetch, Data Cache and Wait-States
- 6.4.8 Access Protection Mechanism for Memories
- 6.4.9 SRAM ECC
- 6.4.10 SRAM Parity
- 6.4.11 Software Test of Parity Logic
- 6.4.12 Software Test of SRAM
- 6.4.13 Memory Power-On Self-Test (MPOST)
- 6.4.14 Background CRC
- 6.4.15 Watchdog for Background CRC
- 6.4.16 Redundant Parity Engine
- 6.4.17 Test of SRAM Parity
- 6.5
On-Chip Communication Including Bus-Arbitration
- 6.5.1 1oo2 Software Voting Using Secondary Free Running Counter
- 6.5.2 DMA Overflow Interrupt
- 6.5.3 Event Timestamping Using IPC Counter
- 6.5.4 Maintaining Interrupt Handler for Unused Interrupts
- 6.5.5 Majority Voting and Error Detection of Link Pointer
- 6.5.6 PIE Double SRAM Comparison Check
- 6.5.7 PIE Double SRAM Hardware Comparison
- 6.5.8 Power-Up Pre-Operational Security Checks
- 6.5.9 Software Check of X-BAR Flag
- 6.5.10 Software Test of ePIE Operation Including Error Tests
- 6.5.11 Disabling of Unused DMA Trigger Sources
- 6.5.12 Software Test of CLB Function Including Error Tests
- 6.5.13 Monitoring of CLB by eCAP or eQEP
- 6.5.14 Lock Mechanism for Control Registers
- 6.5.15 Internal Watchdog (WD)
- 6.5.16 Periodic Software Read Back of SPI Buffer
- 6.5.17 IPC 64-Bit Counter Value Plausibility Check
- 6.6
Digital I/O
- 6.6.1 ECAP Application Level Safety Mechanism
- 6.6.2 ePWM Application Level Safety Mechanism
- 6.6.3 ePWM Fault Detection Using XBAR
- 6.6.4 ePWM Synchronization Check
- 6.6.5 eQEP Application Level Safety Mechanisms
- 6.6.6 eQEP Quadrature Watchdog
- 6.6.7 eQEP Software Test of Quadrature Watchdog Functionality
- 6.6.8 Hardware Redundancy
- 6.6.9 HRPWM Built-In Self-Check and Diagnostic Capabilities
- 6.6.10 Information Redundancy Techniques
- 6.6.11 Monitoring of ePWM by eCAP
- 6.6.12 Monitoring of ePWM by ADC
- 6.6.13 Online Monitoring of Interrupts and Events
- 6.6.14 SDFM Comparator Filter for Online Monitoring
- 6.6.15 SD Modulator Clock Fail Detection Mechanism
- 6.6.16 Software Test of Function Including Error Tests
- 6.6.17 Monitoring of HRPWM by HRCAP
- 6.6.18 HRCAP Calibration Logic Test Feature
- 6.6.19 QMA Error Detection Logic
- 6.7
Analog I/O
- 6.7.1 ADC Information Redundancy Techniques
- 6.7.2 ADC Input Signal Integrity Check
- 6.7.3 ADC Signal Quality Check by Varying Acquisition Window
- 6.7.4 CMPSS Ramp Generator Functionality Check
- 6.7.5 DAC to ADC Loopback Check
- 6.7.6 DAC to Comparator Loopback Check
- 6.7.7 Opens/Shorts Detection Circuit for ADC
- 6.7.8 VDAC Conversion by ADC
- 6.7.9 Disabling Unused Sources of SOC Inputs to ADC
- 6.8
Data Transmission
- 6.8.1 Controller Area Network (MCAN, CAN-FD)
- 6.8.2
ECAT
- 6.8.2.1 EtherCAT MDIO Command Error Indication
- 6.8.2.2 EtherCAT Sync-Manager
- 6.8.2.3 EtherCAT Working Counter Error Indication
- 6.8.2.4 EtherCAT Frame Error Indication
- 6.8.2.5 EtherCAT Physical Layer Error Indication
- 6.8.2.6 PDI Timeout Error Indication
- 6.8.2.7 EtherCAT EEPROM CRC Error Indication
- 6.8.2.8 EtherCAT EEPROM Not Done Error Indication
- 6.8.2.9 EtherCAT Data Link Error Indication
- 6.8.2.10 EtherCAT Phy Link Error Indication
- 6.8.2.11 Sync, GPO Monitoring Using External Monitor
- 6.8.2.12 EtherCAT Enhanced Link Detection With LED
- 6.8.2.13 HW Redundancy of GPIO, FMMU, Sync Manager and SYNC OUT
- 6.8.3 Bit Error Detection
- 6.8.4 CRC in Message
- 6.8.5 DCAN Acknowledge Error Detection
- 6.8.6 DCAN Form Error Detection
- 6.8.7 DCAN Stuff Error Detection
- 6.8.8 EMIF Access Latency Profiling Using On-Chip Timer
- 6.8.9 EMIF Access Protection Mechanism
- 6.8.10 EMIF Asynchronous Memory Timeout Protection Mechanism
- 6.8.11 I2C Access Latency Profiling Using On-Chip Timer
- 6.8.12 Information Redundancy Techniques Including End-to-End Safing
- 6.8.13 I2C Data Acknowledge Check
- 6.8.14 McBSP Receiver Overrun Detection
- 6.8.15 McBSP Receiver Sync Error Detection
- 6.8.16 McBSP Transmitter Sync Error Detection
- 6.8.17 McBSP Transmitter Underflow Detection
- 6.8.18 Parity in Message
- 6.8.19 SCI Break Error Detection
- 6.8.20 SCI Frame Error Detection
- 6.8.21 SCI Overrun Error Detection
- 6.8.22 Software Test of Function Using I/O Loopback
- 6.8.23 SPI Data Overrun Detection
- 6.8.24 Transmission Redundancy
- 6.8.25 FSI Data Overrun/Underrun Detection
- 6.8.26 FSI Frame Overrun Detection
- 6.8.27 FSI CRC Framing Checks
- 6.8.28 FSI ECC Framing Checks
- 6.8.29 FSI Frame Watchdog
- 6.8.30 FSI RX Ping Watchdog
- 6.8.31 FSI Tag Monitor
- 6.8.32 FSI Frame Type Error Detection
- 6.8.33 FSI End of Frame Error Detection
- 6.8.34 FSI Register Protection Mechanisms
- 6.8.35 PMBus Protocol CRC in Message
- 6.8.36 Clock Timeout
- 6.1
C2000 MCU Infrastructure Components
- 7References
- A Safety Architecture Configurations
- B Distributed Developments
- C Terms and Definitions
- D Summary of Safety Features and Diagnostics
- E Glossary
- F Revision History
C Terms and Definitions
- IEC60730: The IEC 60730 standard covers mechanical, electrical, electronic, EMC, and abnormal operation of ac appliances. It is used in the design of design of white goods and other appliances to improve customer safety using software test libraries developed in accordance with this standard.
- IEC61508: Functional safety standard for E/E/PE safety-related systems. This is intended to be a basic functional safety standard applicable to all kinds of industry. It defines functional safety as: “part of the overall safety relating to the EUC (Equipment Under Control) and the EUC control system which depends on the correct functioning of the E/E/PE safety-related systems, other technology safety-related systems and external risk reduction facilities” [4].
- ISO13849: provides safety requirements and guidance for the design and integration of safety-related parts of control systems (SRP/CS), including software design.
- M out of N (MooN) architecture: A safety instrumented system where ‘M’ channels out of ‘N’ channels are required for functionally safe operation. (for example, 2oo3, 2 out of 3 architecture, where majority voting is used to implement a safety function).
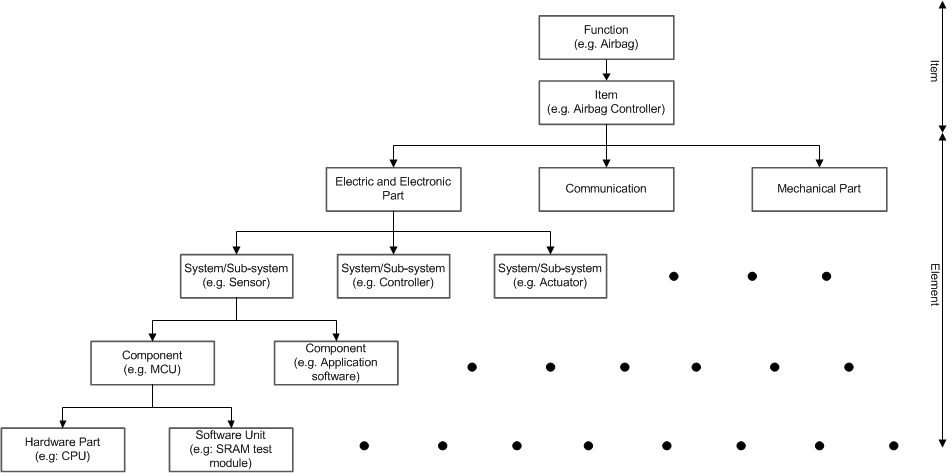 Figure C-1 ISO26262 Illustration of Item, System, Component, Hardware Part and Software Unit
Figure C-1 ISO26262 Illustration of Item, System, Component, Hardware Part and Software Unit - M out of N Channel Architecture with diagnostics (MooND).
- Functional Safety: Part of the overall safety relating to the EUC and the EUC control system that depends on the correct functioning of the E/E/PE safety-related systems and other risk reduction measures
- Item: system or array of systems to implement a function at the vehicle level, to which ISO 26262 is applied (for example, power steering of a car).
- Element: System or part of a system including components, hardware, software, hardware parts, and software units.
- System: set of elements that relates at least a sensor, a controller and an actuator with one another
- Component: Non-system level element that is logically and technically separable and is comprised of hardware parts and software units.
- Hardware part: Hardware that cannot be subdivided (for example, CPU).
- Software unit: Atomic level software component of the software architecture that can be subjected to stand-alone testing (for example, SRAM test module).
- Failure: termination of the ability of an element, to perform a function as required.
- Failure mode: manner in which an element or an item fails.
- Single Point Fault: Fault in an element that is not covered by a safety mechanism and that leads directly to the violation of a safety goal.
- Single-point failure: Failure that results from a single-point fault and that leads directly to the violation of a safety goal.
- Multiple-point fault: Individual fault that, in combination with other independent faults, leads to a multiple-point failure.
- Multiple-point failure: Failure resulting from the combination of several independent faults, which leads directly to the violation of a safety goal. For a multiple-point failure to directly violate a safety goal, presence of all independent faults is necessary.
- Multiple-point fault detection interval: time span to detect multiple-point fault before it can contribute to a multiple-point failure.
- Latent fault: multiple-point fault whose presence is not detected by a safety mechanism nor perceived by the driver within the multiple-point fault detection interval.
- Functional Safety Assessment: Investigation, based on evidence, to judge the functional safety achieved by one or more E/E/PE safety-related systems and/or other risk reduction measures.
- Functional Safety Audit: Systematic and independent examination to determine whether the procedures specific to the functional safety requirements to comply with the planned arrangements are implemented effectively and are suitable to achieve the specified objectives.
- Hazard and Risk Analysis (IEC61508)/Hazard Analysis and Risk Assessment (ISO26262): An end equipment level functional safety analysis that is used to identify safety functions and/or functional safety goals. This process also establishes the SIL (IEC61508) or ASIL (ISO26262), which defines the level of risk reduction necessary per safety function and/or functional safety goal.
- Process Tailoring: The act of changing a development process or functional safety life cycle to match needs of a business engagement. Requirements can be moved from phase to phase or performed by other developers, but removal of process requirements is not allowed.
- Quality Managed: Describes a design element which is developed compliant to applicable quality standards but is not developed compliant to applicable functional safety standards. It may be possible to use a quality managed design element in a specific functional safety design contingent upon results of a functional safety qualification.
- Safety Requirement Decomposition: Safety requirements decomposition is the process in which safety requirements are split into a series of redundant safety requirements at a lower level of abstraction in order to support tailoring of the ASIL (ISO26262) compliance requirements of design elements at the lower level of abstraction. For example, a requirement for a peripheral function with high safety integrity might be addressed by redundant instances of a peripheral with lower safety integrity.
- For the full list of applicable terms and their definitions for ISO26262, see the ISO26262-1:2018, Road vehicles — Functional safety — Part 1: Vocabulary.
- For the full list of applicable terms and their definitions for IEC61508, see the IEC61508, Functional safety of electrical/electronic/programmable electronic safety-related systems – Part 4: Definitions and abbreviations.