SLAU654E November 2015 – February 2019
7.4 Securing the Target Device
Use the -f switch to permanently lock JTAG access to the target device. For older MSPs from the 1xx, 2xx, and 4xx families, this trigger blows the internal poly fuse of the device, thus making the JTAG interface physically and irreversibly unusable. For newer MSPs (for example, from the 5xx and 6xx families) the -f switch programs the electronic fuse or soft fuse (see the device family user's guide for more details). For SimpleLink MSP432 devices, the security feature JTAG/SWD lock will be activated. If you re-connect to the device, a factory reset will be offered. A factory reset will erase main memory and reset all security settings on the device. To force a factory reset without prompt, use -e ERASE_TOTAL.
NOTE
Breakpoint functionality is disabled when the -f switch is used.
MSP Flasher cannot blow the JTAG security fuse of MSP430L092 devices.
MSP430Flasher -n MSP430F5438A -f
Figure 5 shows the console output after running the previous command line.
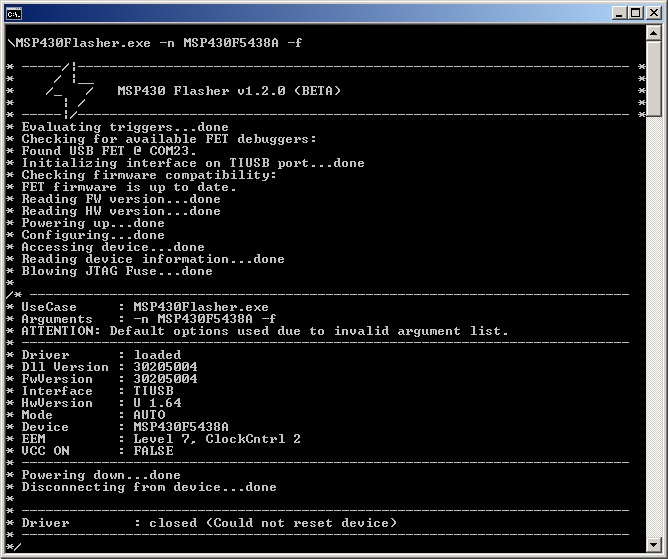 Figure 5. Securing the Target device
Figure 5. Securing the Target device Figure 6 shows the console output after running the following command line to read the device main memory after securing the target device.
MSP430Flasher -n MSP430F5438A -r [out.txt,MAIN]
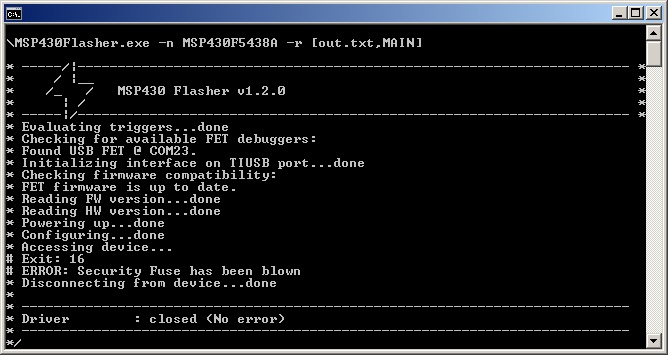 Figure 6. Trying to Access a Secured Target Device
Figure 6. Trying to Access a Secured Target Device