SLAU654E November 2015 – February 2019
7.1 Loading and Executing Target Code From a TXT File
Details:
- Device: MSP430F5438A
- Interface: USB
- Password: N/A
- File: file.txt (in the same directory as the executable)
- Erase Type: ERASE_ALL
- Verification: TRUE
- VCC: ON
NOTE
To load a TI .txt or Intel .hex file, make sure that the file to be loaded is in the same directory as the executable or that a valid path is specified.
The command line to use in this case is:
MSP430Flasher -n MSP430F5438A -w file.txt -v -z [VCC] (-i USB) (-e ERASE_ALL)
NOTE
Triggers -p and -l are not used, because the device does not require a password. Triggers -i and -e may be used but are unnecessary, because USB and ERASE_ALL are the default settings for these parameters, respectively.
Figure 1 shows the console output on entering the previous command line into Windows command prompt if the selected device is connected through the specified COM port.
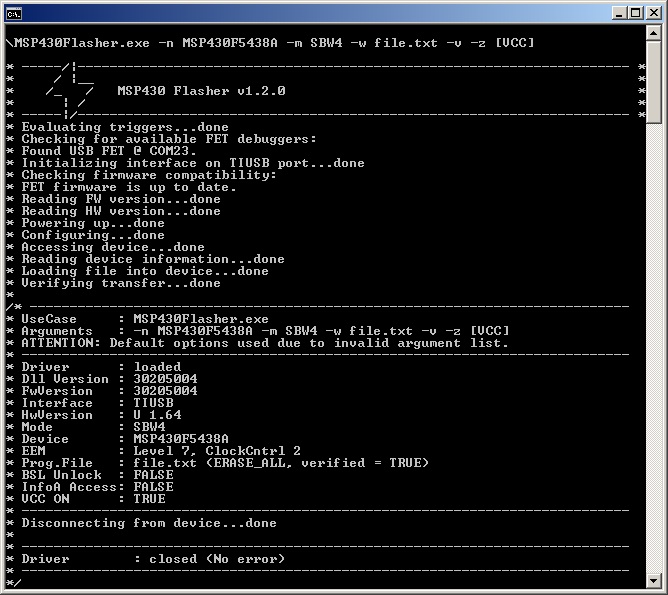 Figure 1. Loading and Executing Target Code From a .txt File
Figure 1. Loading and Executing Target Code From a .txt File