SLUAAL5 September 2022 BQ26100
3 Risk of Using BQ26100 SHA-1 for Authentication
BQ26100 provides a secure enough authentication. But from the description in Section 2, we know that the host (MCU) also need to store the 16 bytes key in the flash. But the MCU flash might be hacked physically and then read out. Once they get all the data in the flash of MCU, then they can try the limited combinations of 16 consecutive bytes data as challenge, with limited time and resource, and find the correct keys, as shown in the Figure 3-1. Figure 3-1 illustrates the partial data in MCU flash.
For example, the first 16 bytes 0x4483111511FB10DD10BF10A210851069 will be tried first. If authentication is failed, then try 0x83111511FB10DD10BF10A21085106910. If still failed, then try 0x111511FB10DD10BF10A210851069104D, and so on.
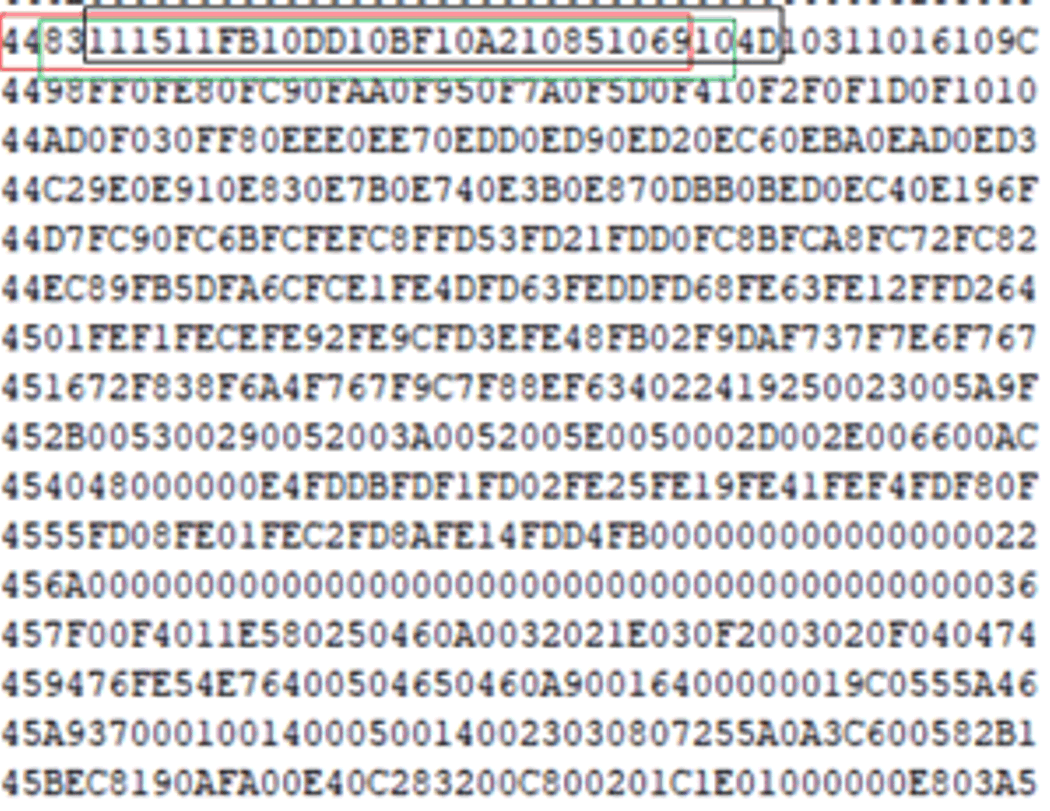 Figure 3-1 Partial Data in MCU
Flash
Figure 3-1 Partial Data in MCU
Flash