SLUAAL5 September 2022 BQ26100
2 BQ26100 and SHA-1 Introduction
Figure 2-1 is the simplified schematic of BQ26100. BQ26100 applies single wire communication SDQ. SDQ pin is a multi-functional pin: communication pin and power supply pin.
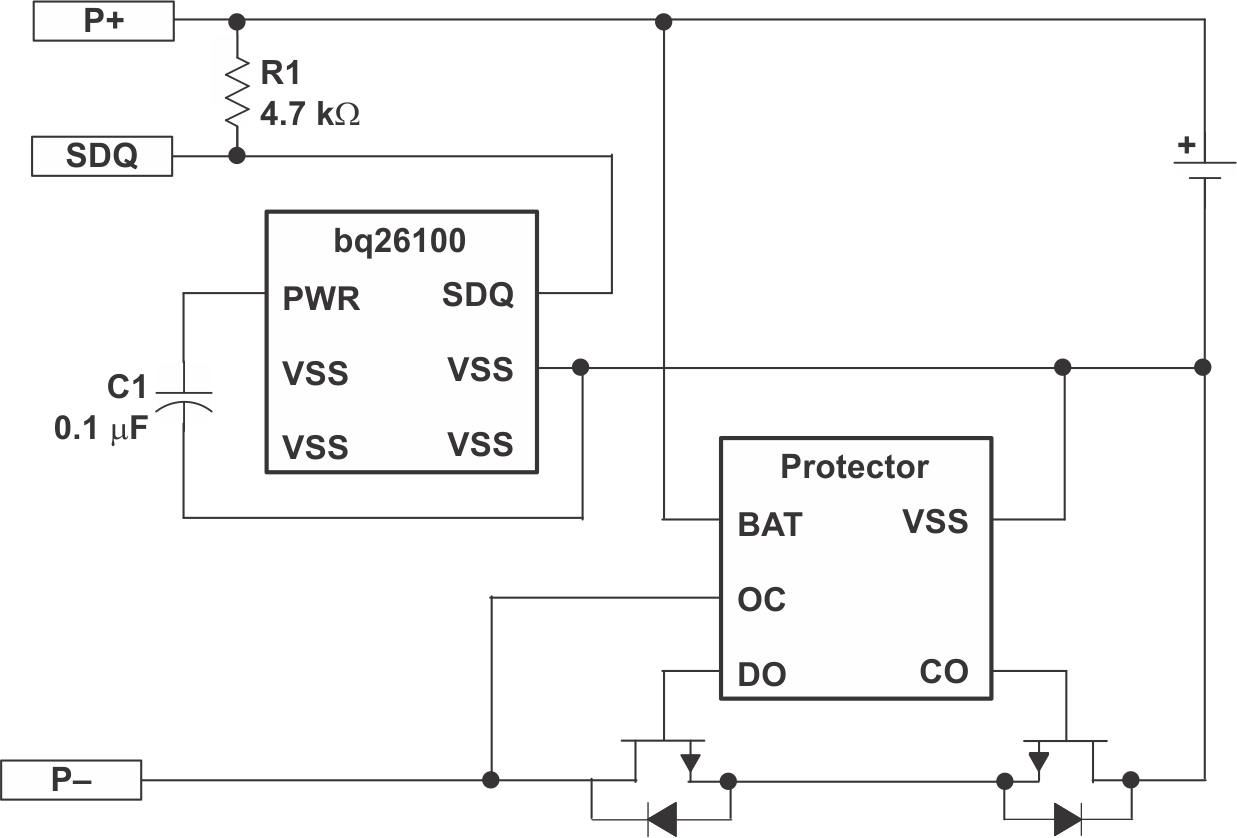 Figure 2-1 Simplified Schematic of
BQ26100
Figure 2-1 Simplified Schematic of
BQ26100BQ26100 embeds SHA-1 authentication algorithm. Figure 2-2 shows the flow of SHA-1 authentication.
- The host and slave store the same 16 bytes key.
- The host generates 20 bytes random number as challenge. And also send to the slave.
- Both the host and slave use the same key, the same challenge, the same function SHA-1 to calculate the results: 20 bytes digest.
- The host read the result from the slave.
- Host compares the two results.
- If the two digests are matched, then consider the slave is qualified.
From the steps above, we can see that the 20 bytes challenge and 20 bytes digest are detectable, and are transmitted transparently through communication line, as shown in Figure 2-2 with green arrows. The third party can easily detect those data with logic analyzer. But theoretically, even they know the challenge and digest, they cannot deduce the SHA-1 key. This is the advantage of SHA-1 authentication.
To enhance the security level of SHA-1 authentication, one simple method is that the host use the first 20 bytes digest as another 20 bytes challenge and run authenticate for the second time.