-
How to Port WOLFSSL Onto TI Sitara AM335 Starterkit
How to Port WOLFSSL Onto TI Sitara AM335 Starterkit
How to Port WOLFSSL Onto TI Sitara AM335 Starterkit
This application report introduces how to integrate the wolfSSL onto TI Sitara RTOS.
Project collateral discussed in this application report can be downloaded from the following URL: http://www.ti.com/lit/zip/spracm5.
Trademarks
All other trademarks are the property of their respective owners.
1 Introduction
WolfSSL is a famous TLS/SSL software solution and it is proven by many worldwide customers. Its quality is robust and the WolfSSL company maintains the security of their product each year.
This document contains:
- Where to get the right WolfSSL code versions
- Which TI RTOS version will be the suitable base for porting
- Step-by-step porting
- Code building
- How to run the demo
2 Hardware and Software Required Stuffs
- Hardware:
- Software:
- WolfSSL for TI TivaC:
- WolfSSL main release
- TI CCS 7.4
- Microsoft Virtual Studio Express 2012
- en_visual_studio_express_2012_for_windows_desktop_x86_web_installer_1001991.exe
3 Step-by-Step Porting
Follow these steps for porting:
- Download the AM335 RTOS SDK.
- Create the example by referencing this: http://processors.wiki.ti.com/index.php/Rebuilding_The_PDK
- Build the PDK.
- Follow the information in Section 4 to merge the WolfSSL required code.
- The pictures in Section 4 have the WolfSSL original code.
- Add the must-have compile option.
- Rebuild the entire project.
4 Merging the WolfSSL Code and Building Regarding the NIMP FTP Example
Create the three sub-folders (see Figure 1) in your code base, then put those folders under the parent folder named: wolfSSL.
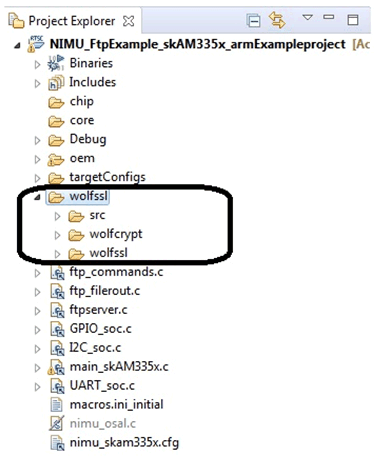 Figure 1. Project Arch to Create Three Subfolders for wolfSSL
Figure 1. Project Arch to Create Three Subfolders for wolfSSL - Copy wolfssl-master\src to (for example):
- Copy wolfssl-master\wolfcrypt\src to (for example):
- Copy the wolfssl-master\wolfssl\ files to (for example):
- Copy the wolfssl-master\wolfssl\wolfcrypt code (without “port” folder”) to (for example):
- Modify some codes:
- In the wolfssl\src\internal.c, add the code as shown in Figure 8.
- wolfssl\src\random_rng_Porting.c
- Add the two parts shown in Figure 10 into the file: nimu_skam335x.cfg.
- In the wolfssl\src\internal.c file, add the two parts:
- wolfSSL_SetIORecv
- wolfSSL_SetIOSend
- Add the “must-have” compile options for wolfSSL.
- Add the Variables for environment including use.
- Adding the variable to the environment.
- Project settings:
- Product settings:
- XDCtools
- SysBios
- PDK
- NDK
- Target config:
- It needs to choose XDS100V2 USB
- Board of device is: SK_AM3358
- Build should be successful.
If you are installing all of the TI packages, then, go to pdk_am335x_1_0_10\packages\MyExampleProjects\NIMU_FtpExample_skAM335x_armExampleproject\wolfssl\src.
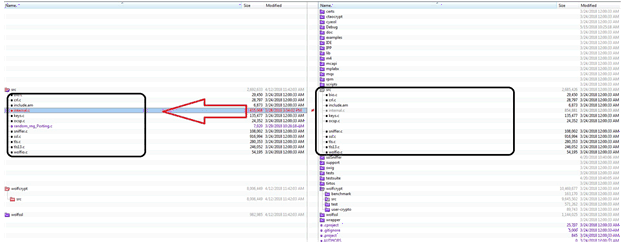 Figure 2. Copy wolfssl\src
Figure 2. Copy wolfssl\src If you are installing all of the TI packages, then, go to pdk_am335x_1_0_10\packages\MyExampleProjects\NIMU_FtpExample_skAM335x_armExampleproject\wolfssl\wolfcrypt\src.
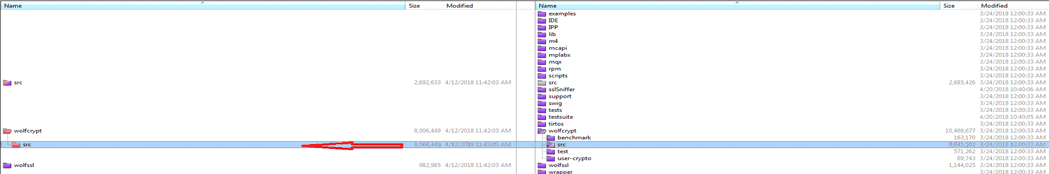 Figure 3. Copy wolfssl\wolfcrypt\src
Figure 3. Copy wolfssl\wolfcrypt\src Do not copy the “port” dir.
Do not copy the .asm .s file.
Figure 4 is marked with “X”.
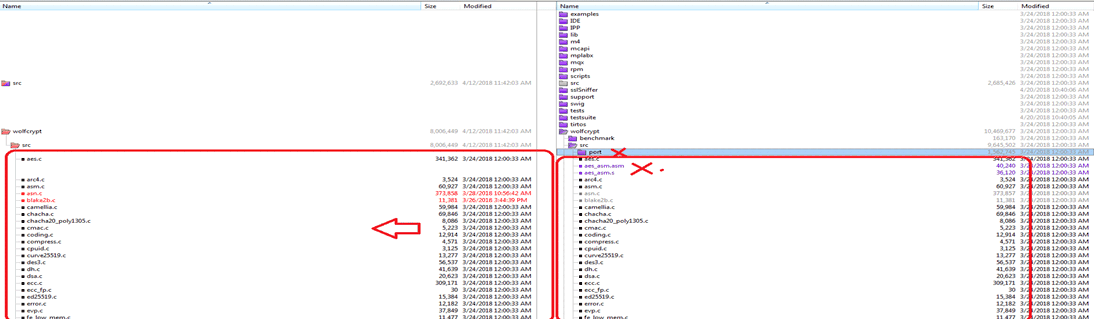 Figure 4. Ignore the .s/.asm Files
Figure 4. Ignore the .s/.asm Files If you are installing all the TI packgeI, then, go to pdk_am335x_1_0_10\packages\MyExampleProjects\ NIMU_FtpExample_skAM335x_armExampleproject\wolfssl\wolfSSL.
 Figure 5. Copy wolfssl\wolfSSL
Figure 5. Copy wolfssl\wolfSSL If you are installing all the TI packge, then, go to pdk_am335x_1_0_10\packages\MyExampleProjects\NIMU_FtpExample_skAM335x_armExampleproject\wolfssl\wolfSSL\wolfcrypt.
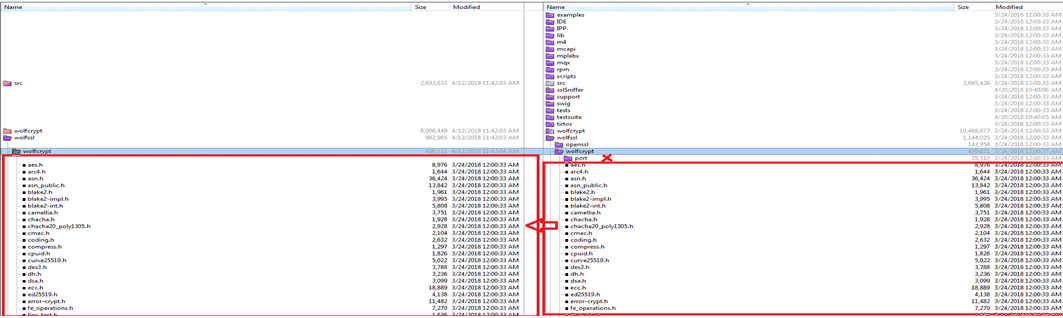 Figure 6. Copy wolfssl\wolfSSL\wolfcrypt
Figure 6. Copy wolfssl\wolfSSL\wolfcrypt In the wolfssl\wolfcrypt\src\random.c, add the code as shown in Figure 7.
 Figure 7. random.c Modification
Figure 7. random.c Modification 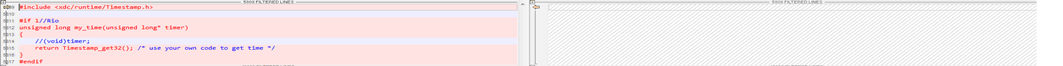 Figure 8. internal.c Modification
Figure 8. internal.c Modification Add a new file (for example):
Reference the random_rng_Porting.c file in this zip file: 2018_5_15_WolfSSL_Importan_Temp_Backup_Client_Server_All_Okay_Release.
Download from here.
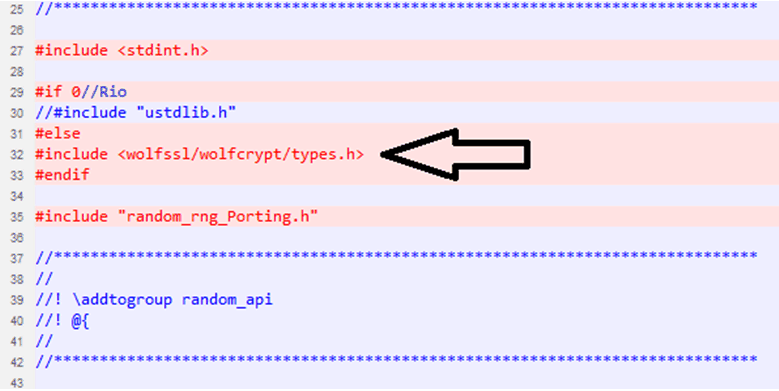 Figure 9. random_rng_Porting.c Modification
Figure 9. random_rng_Porting.c Modification 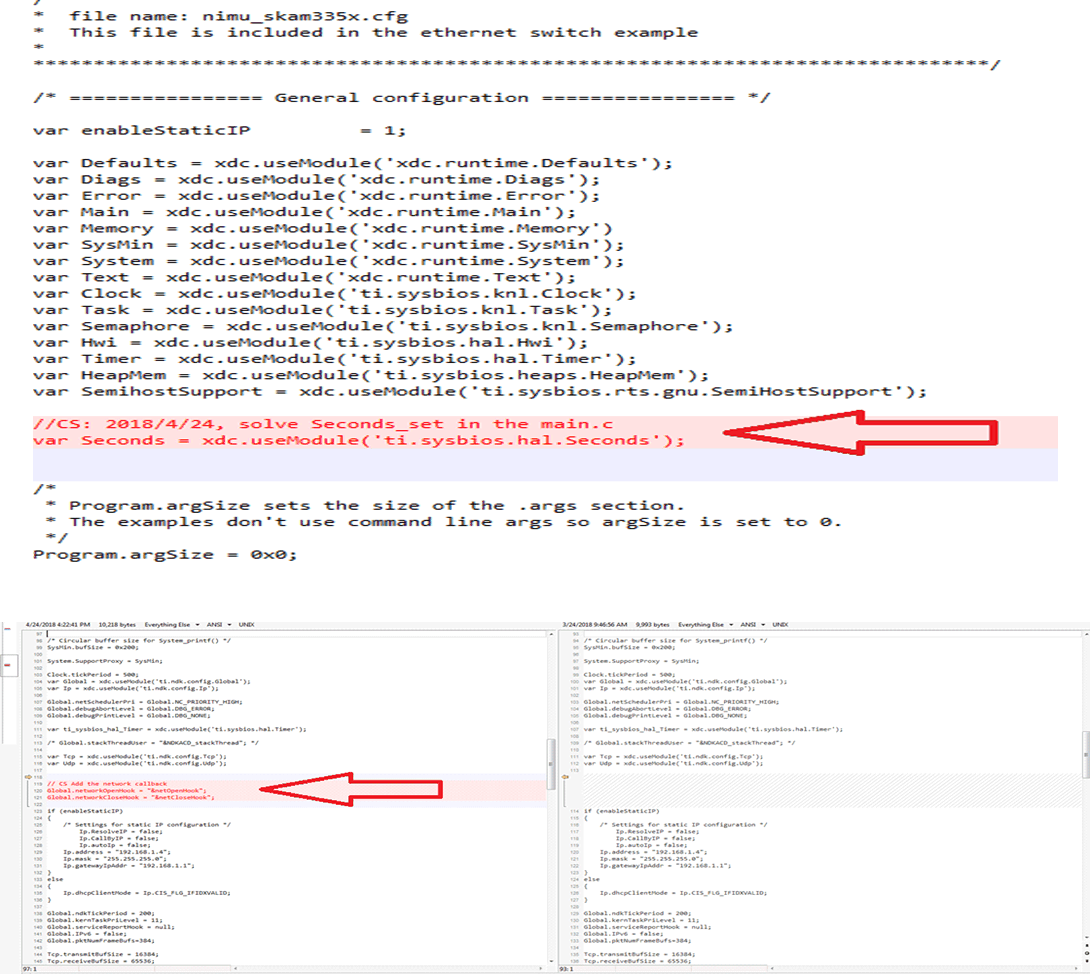 Figure 10. nimu_skam335x.cfg Modification
Figure 10. nimu_skam335x.cfg Modification The first part is to register the user I/O call back:
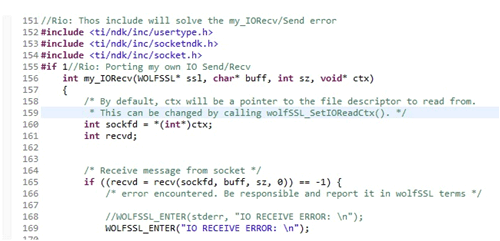 Figure 11. My Own IO Callback Regs
Figure 11. My Own IO Callback Regs Another one is to get the system time, this is related with the NO_ASN_TIME/ASN_TIME config.
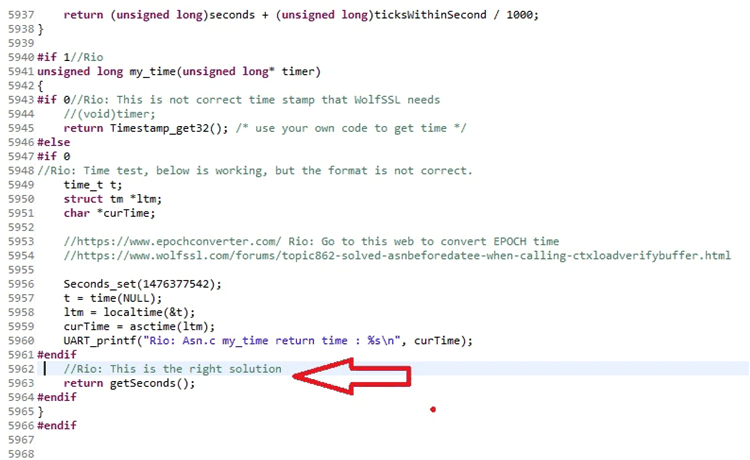 Figure 12. My Time Modification
Figure 12. My Time Modification For example, xNO_FILESYSTEM is to disable the “NO_FILESYSTEM”.
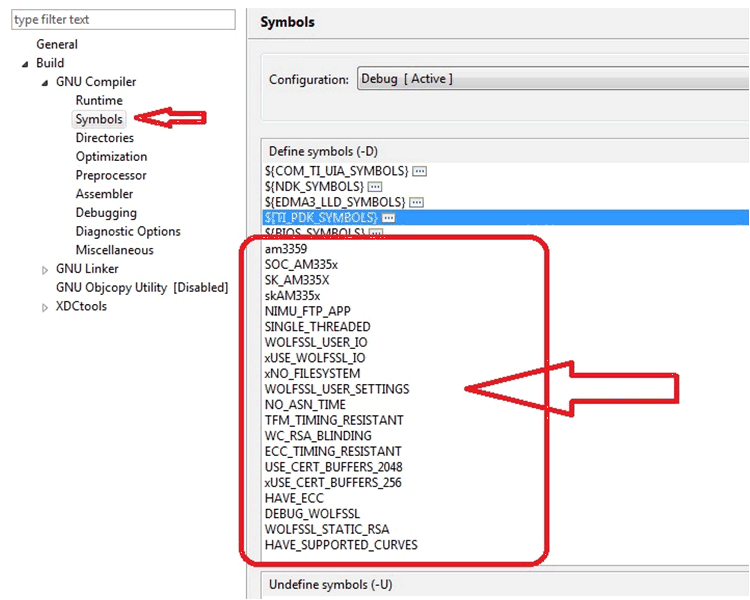 Figure 13. Compile Definition
Figure 13. Compile Definition Add the included folder for the wolfSSL used header file.
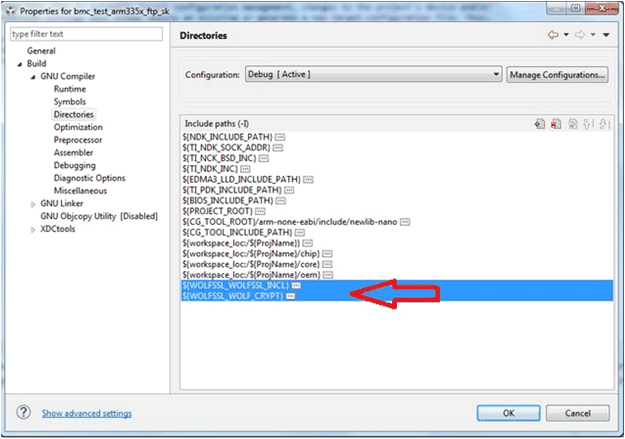 Figure 14. Include Path Setting Part 1
Figure 14. Include Path Setting Part 1 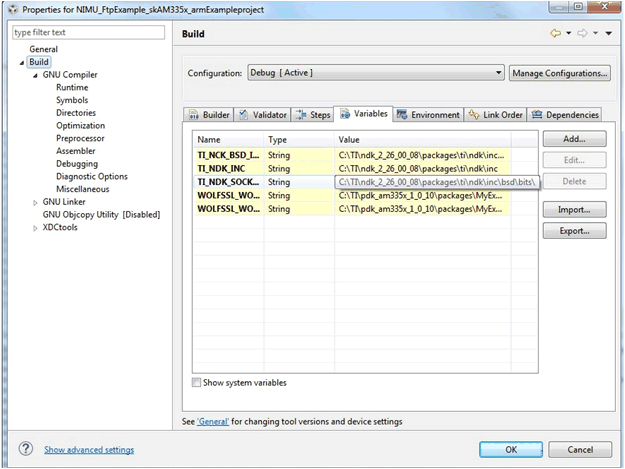 Figure 15. Include Path Setting Part 2
Figure 15. Include Path Setting Part 2 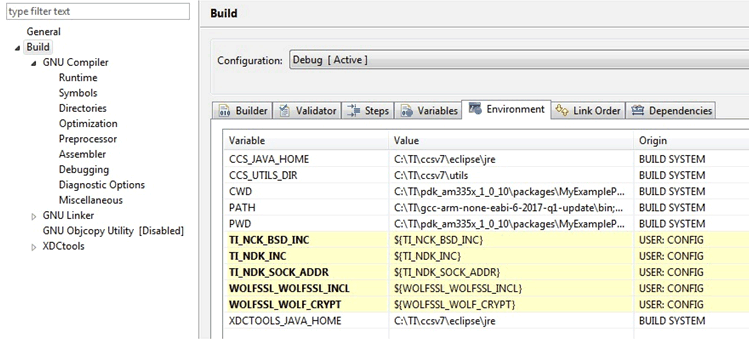 Figure 16. Include Path Setting Part 3
Figure 16. Include Path Setting Part 3 Select the right compiler version and the boards. AM335SK can use the ICE_AM3359.
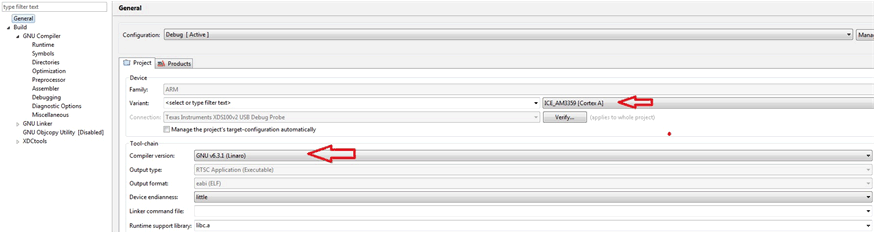 Figure 17. Project Setting
Figure 17. Project Setting Please make sure the right versions of:
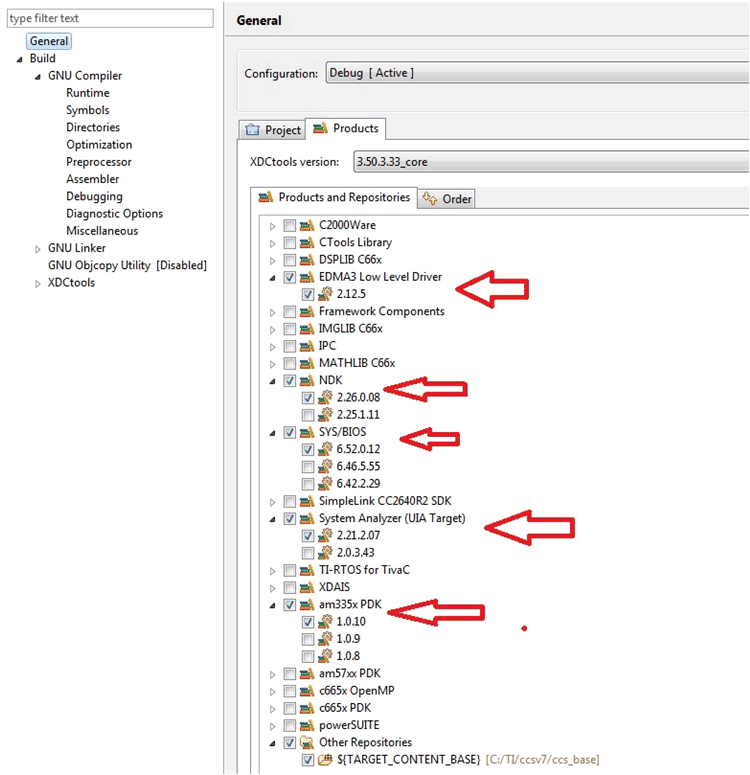 Figure 18. Product Setting
Figure 18. Product Setting The important key for the download image and debug is the JTAG.
You can test the connection while finishing your own setting of the “ccxml.
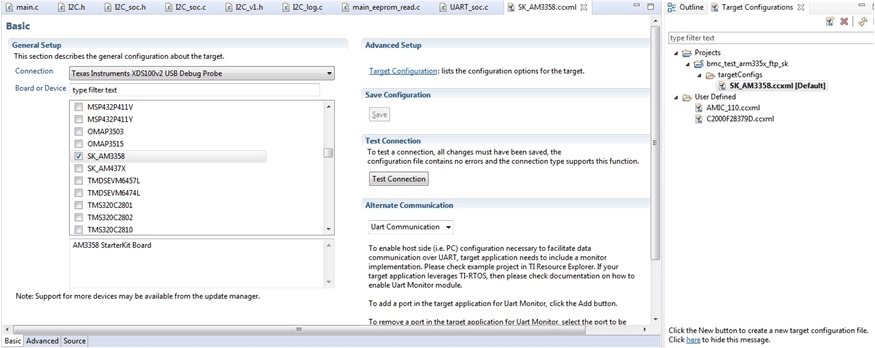 Figure 19. Target Config
Figure 19. Target Config 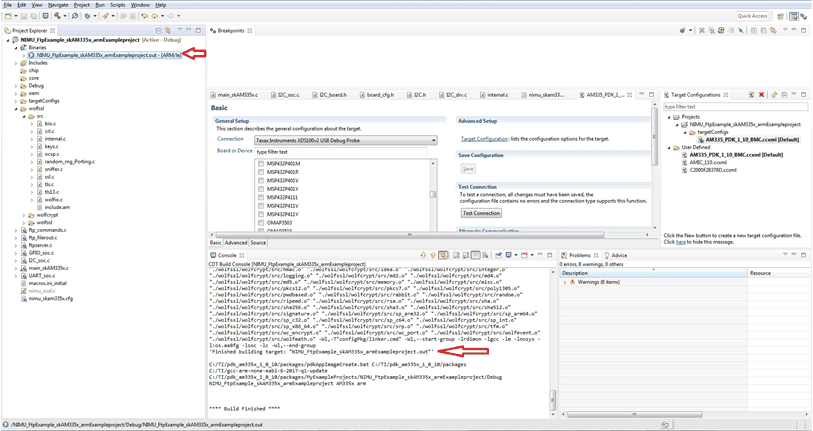 Figure 20. Project Building
Figure 20. Project Building